Russian hackers attacked Western military mission in Ukraine
In 2025, the Asian hacking group Gamaredon (known as "Shuckworm") attacked a Western military mission based in Eastern Europe, as well as military facilities located in Ukraine.
In 2025, the Asian hacking group Gamaredon (known as "Shuckworm") attacked a Western military mission based in Eastern Europe, as well as military facilities located in Ukraine.

In 2025, the Asian hacking group Gamaredon (known as "Shuckworm") attacked a Western military mission based in Eastern Europe, as well as military facilities located in Ukraine.
Symantec threat researchers report that the campaign began in February 2025 and continued until March, when hackers deployed an updated version of the GammaSteel malware to steal data.
The attackers used an updated version of their GammaSteel tool, which steals data from victims' networks.
During the investigation, researchers noticed a new value under the UserAssist key in the Windows registry of the compromised system, indicating that the infection started from an external drive from the files.lnk shortcut file.
Next, the heavily obfuscated script creates and runs two files. The first handles command-and-control (C2) communication, resolves the server address using legitimate services, and connects to Cloudflare-protected URLs.
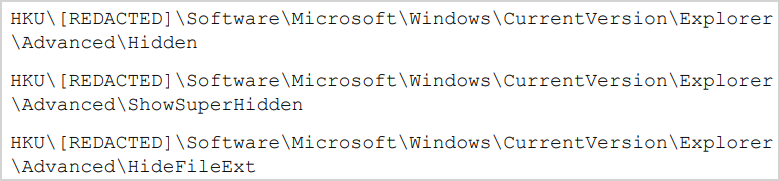
The second file controls the propagation mechanism to infect other removable and network drives using LNK files, and also hides certain folders and system files to hide the compromise.
Gamaredon then used a PowerShell reconnaissance script that could take screenshots of the infected device and collect information about installed antivirus tools, files, and running processes.
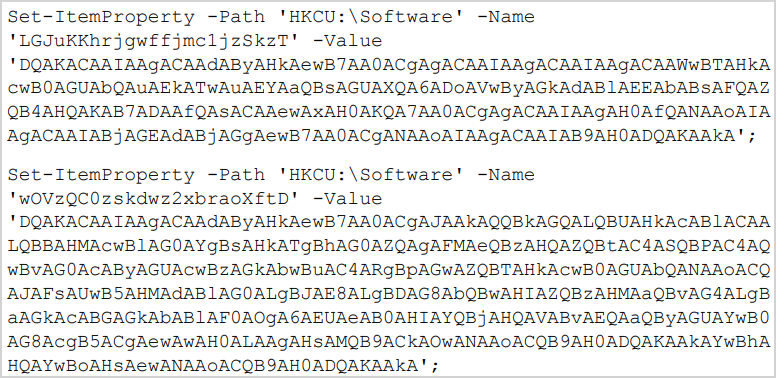
The final payload used in the attacks described is a PowerShell-based version of GammaSteel that is stored in the Windows registry.
The malware can steal documents (.DOC, .PDF, .XLS, .TXT) from various locations such as Desktop, Documents, and Downloads, confirming Gamaredon's ongoing interest in espionage.
Ultimately, the malware uses “certutil.exe” to hash files and steals them using PowerShell web requests. If the infiltration fails, Gamaredon uses cURL over Tor to transfer the stolen data.
Finally, a new key is added to "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" to establish persistence on the target computer.
Symantec notes that various improvements to the TTP threat group (tactics, techniques, and procedures) increase the risks that Gamaredon attackers pose to Western networks.


